Tech News Blog

What Is a Data Policy? Building Smart Data Governance for Secure, Productive Businesses
Data is the engine that drives today’s organizations — shaping decisions, customer experiences, compliance, and long-term growth. But without clear guidance on how data is collected, stored, protected, and used, that same data can become a serious risk. At Crown...

What Is a Data Policy? Building Smart Data Governance for Secure, Productive Businesses
Data is the engine that drives today’s organizations — shaping decisions, customer experiences, compliance, and long-term growth. But without clear guidance on how data is collected, stored, protected, and used, that same data can become a serious risk. At Crown...
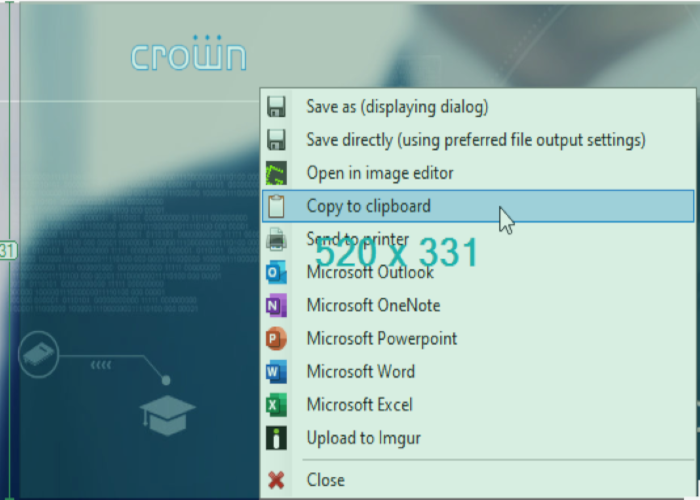
Top 5 Screenshot and Capture Tools
They say a picture is worth a thousand words, and if you’ve been stuck in long work-oriented email chains, you probably know why…
Latest news
Are “cold emails” ever legitimate?
With all of the emphasis on phishing and social engineering scams, it might be easy to lose sight of old-fashioned swindles. While there are some cutting-edge techniques out there for tricking you into handing over private information (like login/password or payment...
IT Change Management: Navigating The Importance, Types and Best Practices
Businesses constantly have to adjust to new trends in today's fast-paced environment. They go through digital transformation by utilizing technology to take advantage of opportunities and solve problems. However, putting new programs or systems into place isn't always...
Should Your Organization Voluntarily Comply With Cybersecurity Standards?
As a small- to medium-sized organization, it might be hard to see the benefits of implementing security standards like NIST 800-171, CMMC. or HIPAA (Health Insurance Portability and Accountability). It could seem cumbersome or overkill to align your operations with...
Today’s best ways to call internationally
It’s possible that you’ve noticed that the least important part of your phone is how it serves as a telephone. Now that mobile devices are (rightly) thought of as an ultra-portable computing device, it can be easy to overlook how you’ll stay in touch when traveling...
Bridge the Gap Between Your Mobile Device and Your Computer
Windows Phone Link is the newest way to integrate your phone and your desktop. Choosing which device to use for the most productivity can be fairly simple: writing intensive tasks are usually done more effectively at a device with a physical keyboard while phones have...
How to Check Network for Malware and Tips for Detecting Malware Attacks
The term “malicious network activity” refers to any action that aims to harm, compromise, or abuse a network’s security in any way. If you can’t protect the network from these threats, things can be pretty awful. But before that, you need to check the network to see...
How to Stop Spam Text From Email to Keep Your Email Safe and Spam-Free
Spam can now enter your mobile devices from multiple directions. It could appear as annoying emails, texts, or phone calls. Previously, email was the digital equivalent of postal mail, but now it has your phone numbers. This means that you may also get spam SMS and...
Capture the Flag, but with Ubiquiti Routers and on a Geopolitical Scale
You may have seen some headlines over the past three weeks regarding Ubiquiti routers. Talk of “botnets” and the Department of Justice dismantling Russian malware is pretty splashy. Reading only the headlines, however, won’t give you a sense of the scale of the...
What is IT Support Technician and How do They Work?
IT, or information technology, is a broad field. It includes a variety of jobs, such as engineers, software developers, webmasters, and IT support technicians. The first three examples we just gave could need the help of an IT support technician at some point. But...
Top IT Management Frameworks for Businesses
It can be hard for an organization to make sure that its IT (information technology) strategy, processes, and resources all align with its goals and needs. Many different frameworks say they can help with that, but which one is the best? Or is there any direct answer...
Teams vs Teams Premium: Is It Worth Upgrading to Premium Teams?
Your organization might already be using Microsoft Teams for all of your office communications, but you might not have heard of Teams Premium. It's an offering from Microsoft that contains a few serious features for stepping up your company's branding and...
Top 5 Steps to Securing Microsoft 365
In our last blog post, we mentioned some of the biggest security risks to your company's Microsoft 365 suite. It may have seemed like there were a lot of concerns to have over your data's confidentiality and availability-which is right, your data's security is your...
What Is Facilities Management IT: Knowing the Significant Roles and Benefits
Information technology has transformed facility management in the last few decades. In today's fast-paced world, businesses need automated facility management for a sustainable future. This guide will describe the significance of IT in facility management. What Is...
Protect Your Devices with a Home Networking Firewall
Numerous harmful programs and hackers are active online, and they want to steal your personal information or get into your computer network system. A home networking firewall keeps those hackers from getting into your home network, just like a security fence does....
The Ultimate Guide to Effective IT Environments Management: Benefits and Challenges
Today’s businesses depend on technology to run their daily tasks and get the most work done. Using technology the right way makes the workplace more efficient. The practice also cuts down on costs and improves communication. However, the way a business manages its IT...
Top 5 Security Threats in Microsoft 365
It's common in the cybersecurity world to note that anything that creates better convenience will also expose users and administrators to more risks. The easier it is to access things, in other words, the less secure those things are. If your organization uses all of...
Demand Management in IT: A Revolutionary Solution in Business Success
A business’s success depends on its ability to guess what customers may want and make sure it has the resources to meet those needs. This is true for IT as well. It is getting harder for IT professionals to provide high-quality services quickly and cheaply while also...















